New SecuriDropper Malware Bypasses Android 13 Restrictions, Disguised as Legitimate Applications
A new malware is bypassing an Android 13 security measure that restricts permissions to apps downloaded out of the legitimate Google Play Store.
A new report from ThreatFabric, a fraud protection company, exposes SecuriDropper malware, which is capable of bypassing Android 13 restricted settings. The malware makes Android consider the installation as coming from the Google Play Store, though in reality it isn’t.
It’s highly recommended for organizations to use Mobile Device Management solutions and methods to enable more control on employees’ Android devices and to restrict installing apps on their devices by using a list of approved applications and forbidding any other.
Jump to:
What are Android 13’s restricted settings?
Android 13 introduced a new security feature called restricted settings. This new feature prevents sideloaded applications (i.e., downloaded out of the Google Play Store) from directly requesting accessibility settings and notification listener access — two features that are often abused by malware according to ThreatFabric’s researchers.
On Android systems, applications downloaded from the legitimate Google Play Store aren’t subject to the same process as those not originating from it. The main reason why is that applications that have made it successfully to the Google Play Store have provided more information and visibility and have passed different security tests to ensure they don’t contain malware functionalities. Therefore, applications from the Google Play Store aren’t concerned by the restricted settings feature.
Applications downloaded from the Play Google Store use a specific installation method — a “session-based” package installer — that isn’t normally used by sideloaded applications.
Meet SecuriDropper malware
The SecuriDropper malware uses the same installation method as legitimate software from the legitimate Google Play Store. After being executed by the unsuspecting user, the malware requests two key permissions: Read & Write External Storage and Install & Delete Packages.
Once permissions are given, the malware checks if it already exists on the device; if it does, the malware runs, and if it doesn’t, the malware shows the user a message telling them something went wrong and the user needs to click a reinstall button. The message is different based on the device’s location and language configured.
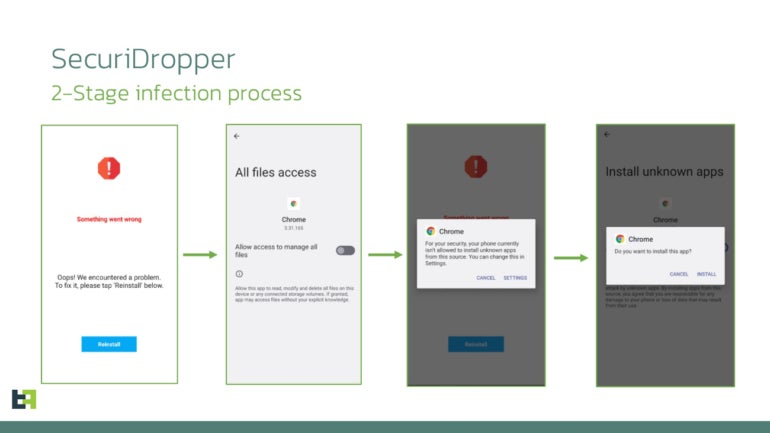
When done, the session-based installation starts, and the user is asked for permission to enable the Accessibility Service, which becomes possible due to the bypass of the restricted settings feature (Figure A).
Figure A
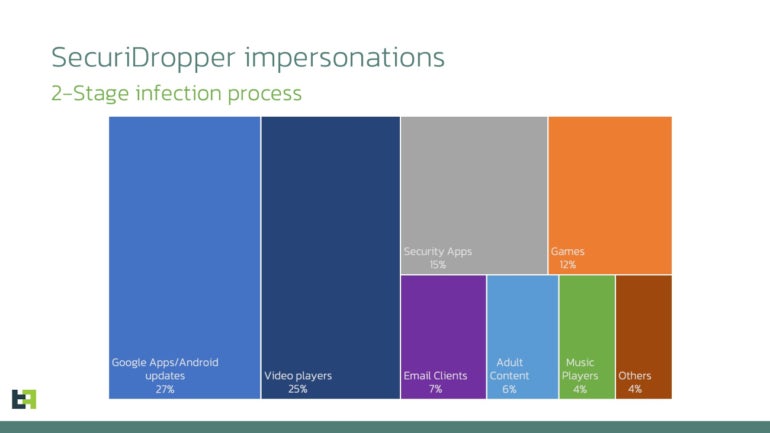
The malware has been observed disguising itself as various Android applications such as Google Apps or Android updates (27%), video players (25%), security applications (15%) or games (12%), followed by email clients, adult content, music players and other apps (Figure B).
Figure B
SecuriDropper’s various final payloads
Any kind of malicious code could be dropped and installed by SecuriDropper, as the malware’s final goal is to install other malware on infected devices. ThreatFabric observed two campaigns using SecuriDropper.
The first one is an attack campaign delivering SpyNote, a malware with remote administration tool features. The malicious payload was being distributed through phishing websites and deployed by SecuriDropper. The SpyNote malware, which is able to capture sensitive information on the device, as well as steal SMS and call logs and take screenshots, absolutely needs permissions that would be unavailable due to Android’s restricted settings. Its installation via SecuriDropper enables the SpyNote malware to keep infecting devices, even on Android 13, without needing to change its code.
In another attack campaign, SecuriDropper was observed installing the ERMAC banking trojan. The malware was deployed via Discord, a communication tool previously used primarily by gamers but increasingly utilized by other communities, including corporate entities.
More malware will use this technique
Different malware families will use this technique in the future. One service that’s already using this technique is Zombinder.
As reported by ThreatFabric, the DarkNet platform Zombinder started advertising for its new version that bypasses Android 13 restricted settings. The Zombinder service allows an attacker to successfully bind a legitimate application with malware. When the infection is done, the legitimate application runs normally, while the malware is being executed in the background, unnoticed.
Zombinder also sells builders with the Android 13 restrictions bypass capability. The builders from Zombinder are software capable of dropping malware on an infected system (aka dropper), sold at $1,000 USD.
As written by ThreatFabric, “the emergence of services like Zombinder are indications of a booming market in cybercrime, offering builders and tools for evading Android 13’s defenses. It is a testament to the resourcefulness of those seeking to exploit security vulnerabilities for their gain.”
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.
A new malware is bypassing an Android 13 security measure that restricts permissions to apps downloaded out of the legitimate Google Play Store.
A new report from ThreatFabric, a fraud protection company, exposes SecuriDropper malware, which is capable of bypassing Android 13 restricted settings. The malware makes Android consider the installation as coming from the Google Play Store, though in reality it isn’t.
It’s highly recommended for organizations to use Mobile Device Management solutions and methods to enable more control on employees’ Android devices and to restrict installing apps on their devices by using a list of approved applications and forbidding any other.
Jump to:
What are Android 13’s restricted settings?
Android 13 introduced a new security feature called restricted settings. This new feature prevents sideloaded applications (i.e., downloaded out of the Google Play Store) from directly requesting accessibility settings and notification listener access — two features that are often abused by malware according to ThreatFabric’s researchers.
On Android systems, applications downloaded from the legitimate Google Play Store aren’t subject to the same process as those not originating from it. The main reason why is that applications that have made it successfully to the Google Play Store have provided more information and visibility and have passed different security tests to ensure they don’t contain malware functionalities. Therefore, applications from the Google Play Store aren’t concerned by the restricted settings feature.
Applications downloaded from the Play Google Store use a specific installation method — a “session-based” package installer — that isn’t normally used by sideloaded applications.
Meet SecuriDropper malware
The SecuriDropper malware uses the same installation method as legitimate software from the legitimate Google Play Store. After being executed by the unsuspecting user, the malware requests two key permissions: Read & Write External Storage and Install & Delete Packages.
Once permissions are given, the malware checks if it already exists on the device; if it does, the malware runs, and if it doesn’t, the malware shows the user a message telling them something went wrong and the user needs to click a reinstall button. The message is different based on the device’s location and language configured.
When done, the session-based installation starts, and the user is asked for permission to enable the Accessibility Service, which becomes possible due to the bypass of the restricted settings feature (Figure A).
Figure A
The malware has been observed disguising itself as various Android applications such as Google Apps or Android updates (27%), video players (25%), security applications (15%) or games (12%), followed by email clients, adult content, music players and other apps (Figure B).
Figure B

SecuriDropper’s various final payloads
Any kind of malicious code could be dropped and installed by SecuriDropper, as the malware’s final goal is to install other malware on infected devices. ThreatFabric observed two campaigns using SecuriDropper.
The first one is an attack campaign delivering SpyNote, a malware with remote administration tool features. The malicious payload was being distributed through phishing websites and deployed by SecuriDropper. The SpyNote malware, which is able to capture sensitive information on the device, as well as steal SMS and call logs and take screenshots, absolutely needs permissions that would be unavailable due to Android’s restricted settings. Its installation via SecuriDropper enables the SpyNote malware to keep infecting devices, even on Android 13, without needing to change its code.
In another attack campaign, SecuriDropper was observed installing the ERMAC banking trojan. The malware was deployed via Discord, a communication tool previously used primarily by gamers but increasingly utilized by other communities, including corporate entities.
More malware will use this technique
Different malware families will use this technique in the future. One service that’s already using this technique is Zombinder.
As reported by ThreatFabric, the DarkNet platform Zombinder started advertising for its new version that bypasses Android 13 restricted settings. The Zombinder service allows an attacker to successfully bind a legitimate application with malware. When the infection is done, the legitimate application runs normally, while the malware is being executed in the background, unnoticed.
Zombinder also sells builders with the Android 13 restrictions bypass capability. The builders from Zombinder are software capable of dropping malware on an infected system (aka dropper), sold at $1,000 USD.
As written by ThreatFabric, “the emergence of services like Zombinder are indications of a booming market in cybercrime, offering builders and tools for evading Android 13’s defenses. It is a testament to the resourcefulness of those seeking to exploit security vulnerabilities for their gain.”
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.
