Twitter Rolls Out Encrypted Messaging, Don’t Trust It
Twitter did it. The company met a deadline and released something on the promised date under Elon Musk’s leadership. The social media platform put out its first-ever encrypted messaging option late on Wednesday night, just under the wire. Yet in the mad dash to deliver, the site seems to have made some confusing compromises, as outlined in a Twitter blogpost.
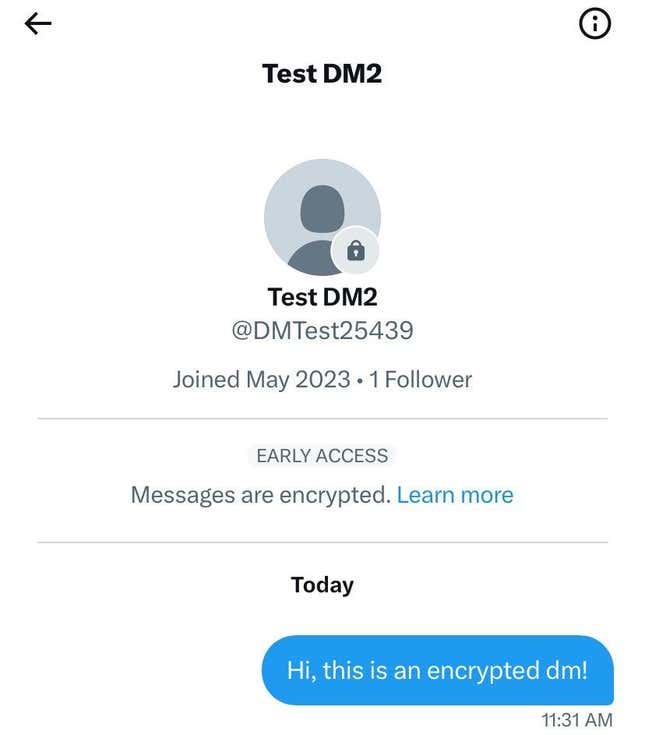
Encrypted DMs on Twitter have been years in the making. The platform first began hinting at and exploring the possibility of secure messages about a decade ago. However, it dropped the concept multiple times after a few false starts, without offering much explanation—as in 2018 when the site seemed to be testing a feature that was never released. Finally though, the bluebird app has encryption—wherein data is encoded upon sending a DM, and decoded at the point of receipt.
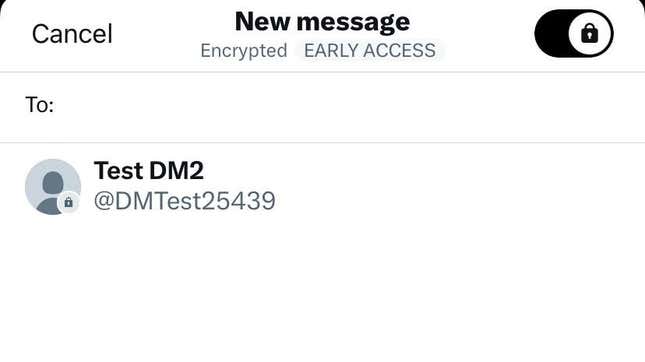
For online privacy writ large it’s undoubtedly a good thing. But Twitter’s version of encryption comes with some major caveats. For one, it is only available to “verified” users, meaning those with access are almost entirely people willing to pay $8 a month for Twitter Blue. Both parties in an encrypted Twitter exchange need to be verified for the feature to work.
Second, it is “opt-in,” which means users have to consciously choose encryption every time. That’s versus the security gold standard of default encryption. Facebook/Meta, for instance, faced years of flack from privacy experts over its own opt-in Messenger end-to-end encryption, which only recently became the default setting.
Then there’s the user limitations. Twitter’s version of secured DMs only allows for the transmission of text. Picture and other media messages cannot currently be encrypted on the platform. Only one-on-one conversations are covered, group messages aren’t. There’s no avenue for reporting abusive encrypted messages. All of these are features readily available on other, well-respected encrypted messaging platforms like Signal, Meta’s Messenger, and WhatsApp. Moreover, neither of those options costs money.
For Matthew Green, a computer scientist and cryptographer at Johns Hopkins University, the aforementioned issues of opt-in, pay to play, and limited usability all make Twitter’s encryption offering worse than much of what’s available elsewhere. “Encryption is an important safety feature,” he told Gizmodo in a phone call. “Unfortunately, they’re only going to provide safety for the people who have paid.”
“Some encryption is better than no encryption,” Green noted. Yet all encryption isn’t equal, and from Twitter’s starting point, “it might be hard to make it good encryption.” In the broadest sense, the privacy tech expert said he’s excited about Twitter’s move towards increased messaging security: “It’s one of the few positive features I’ve seen come out of Twitter in the last few months.” But he has reservations—from the surface level down to the feature’s very foundation.
For now, he maintains that the best use for Twitter messages is to exchange a WhatsApp or Signal number. “That’s the best use of Twitter DMs until anyone knows how good this thing is.”
A Deeper Dive into Twitter’s Encryption Failings
Beyond the user-facing let downs, on the back-end, there are additional weak spots in Twitter’s new security setting. To the company’s credit, it is upfront that its first stab at encrypted DMs isn’t perfect. “When it comes to Direct Messages, the standard should be, if someone puts a gun to our heads, we still can’t access your messages,” the Wednesday blogpost reads, quoting a previous tweet from Musk. “We’re not quite there yet,” it continues.
As Twitter points out in its own statement, its version of encryption doesn’t necessarily protect against “man-in-the-middle” attacks. This means a technically competent bad actor or Twitter itself could theoretically intercept messages without the knowledge of the sender. Because of this weakness, Twitter’s version of encryption is not necessarily end-to-end—again a security gold-standard that Signal, WhatsApp, Messenger, and others offer.
Man-in-the-middle attacks are a security “edge case” said Green, that most probably don’t need to worry about. “It’s a sophisticated attack that, yes, technically could happen,” but it’s less likely than all of the other multitude ways messaging privacy could be compromised. Twitter says it plans to work on improving this vulnerability moving forward. Still though, it’s another ding against Musk’s platform. Yet, much more concerning to Green, is Twitter’s lack of one other generally standard encryption mechanism called “forward secrecy,” also noted in the company’s blog.
“All of the [cryptography] people I know are kind of baffled by that,” he told Gizmodo. With forward secrecy, the encryption key that protects a user’s privacy changes with every message. In practice, it means that if your phone or computer are hacked and the perpetrator gets access to your existing communications and decryption key, they at least won’t be able to intercept or see future messages. “It’s kind of table stakes for all modern encryption protocols,” Green said.
But not for Twitter. The company further says it has no intent to institute a forward secrecy protocol. “We don’t plan to address this limitation,” it wrote.
To Green, it’s “a big red flag.” Modern encryption is generally based on the open-source Signal Protocol. If Twitter were working like basically every other tech company, it would’ve used this readily available, powerful and well-tested code resource to develop its encryption. This would’ve guaranteed changing encryption keys. The fact that the platform didn’t is “super mysterious.” On it’s own, the lack of forward secrecy is “kind of bad,” said Green, but the broader implication that Twitter went completely in-house and designed it’s own cryptography is even more worrying.
As far as he knows, Twitter doesn’t have many cryptographic experts on staff. After Musk’s purge, the platform doesn’t have that many people on staff, period. Encryption is “a very hard thing to get right,” Green said. If Twitter didn’t build on the existing, open source expertise that’s widely available “maybe they made it up themselves, and that’s where people make big mistakes,” the JHU professor added.
Both Green and the company’s blogpost expressed hopes that Twitter’s encryption feature will improve down the line. But the forward secrecy failing gives the security expert pause. If Twitter has made mistakes independently developing this first release of secure messaging, those issues will reverberate throughout the platform in perpetuity. “It seems like they made some foundational choices that might not be great,” Green said. “If you build a bad basement on a house, you’re gonna be fighting with problems forever.”
Twitter did it. The company met a deadline and released something on the promised date under Elon Musk’s leadership. The social media platform put out its first-ever encrypted messaging option late on Wednesday night, just under the wire. Yet in the mad dash to deliver, the site seems to have made some confusing compromises, as outlined in a Twitter blogpost.
Encrypted DMs on Twitter have been years in the making. The platform first began hinting at and exploring the possibility of secure messages about a decade ago. However, it dropped the concept multiple times after a few false starts, without offering much explanation—as in 2018 when the site seemed to be testing a feature that was never released. Finally though, the bluebird app has encryption—wherein data is encoded upon sending a DM, and decoded at the point of receipt.
For online privacy writ large it’s undoubtedly a good thing. But Twitter’s version of encryption comes with some major caveats. For one, it is only available to “verified” users, meaning those with access are almost entirely people willing to pay $8 a month for Twitter Blue. Both parties in an encrypted Twitter exchange need to be verified for the feature to work.
Second, it is “opt-in,” which means users have to consciously choose encryption every time. That’s versus the security gold standard of default encryption. Facebook/Meta, for instance, faced years of flack from privacy experts over its own opt-in Messenger end-to-end encryption, which only recently became the default setting.
Then there’s the user limitations. Twitter’s version of secured DMs only allows for the transmission of text. Picture and other media messages cannot currently be encrypted on the platform. Only one-on-one conversations are covered, group messages aren’t. There’s no avenue for reporting abusive encrypted messages. All of these are features readily available on other, well-respected encrypted messaging platforms like Signal, Meta’s Messenger, and WhatsApp. Moreover, neither of those options costs money.

For Matthew Green, a computer scientist and cryptographer at Johns Hopkins University, the aforementioned issues of opt-in, pay to play, and limited usability all make Twitter’s encryption offering worse than much of what’s available elsewhere. “Encryption is an important safety feature,” he told Gizmodo in a phone call. “Unfortunately, they’re only going to provide safety for the people who have paid.”
“Some encryption is better than no encryption,” Green noted. Yet all encryption isn’t equal, and from Twitter’s starting point, “it might be hard to make it good encryption.” In the broadest sense, the privacy tech expert said he’s excited about Twitter’s move towards increased messaging security: “It’s one of the few positive features I’ve seen come out of Twitter in the last few months.” But he has reservations—from the surface level down to the feature’s very foundation.
For now, he maintains that the best use for Twitter messages is to exchange a WhatsApp or Signal number. “That’s the best use of Twitter DMs until anyone knows how good this thing is.”
A Deeper Dive into Twitter’s Encryption Failings
Beyond the user-facing let downs, on the back-end, there are additional weak spots in Twitter’s new security setting. To the company’s credit, it is upfront that its first stab at encrypted DMs isn’t perfect. “When it comes to Direct Messages, the standard should be, if someone puts a gun to our heads, we still can’t access your messages,” the Wednesday blogpost reads, quoting a previous tweet from Musk. “We’re not quite there yet,” it continues.
As Twitter points out in its own statement, its version of encryption doesn’t necessarily protect against “man-in-the-middle” attacks. This means a technically competent bad actor or Twitter itself could theoretically intercept messages without the knowledge of the sender. Because of this weakness, Twitter’s version of encryption is not necessarily end-to-end—again a security gold-standard that Signal, WhatsApp, Messenger, and others offer.
Man-in-the-middle attacks are a security “edge case” said Green, that most probably don’t need to worry about. “It’s a sophisticated attack that, yes, technically could happen,” but it’s less likely than all of the other multitude ways messaging privacy could be compromised. Twitter says it plans to work on improving this vulnerability moving forward. Still though, it’s another ding against Musk’s platform. Yet, much more concerning to Green, is Twitter’s lack of one other generally standard encryption mechanism called “forward secrecy,” also noted in the company’s blog.
“All of the [cryptography] people I know are kind of baffled by that,” he told Gizmodo. With forward secrecy, the encryption key that protects a user’s privacy changes with every message. In practice, it means that if your phone or computer are hacked and the perpetrator gets access to your existing communications and decryption key, they at least won’t be able to intercept or see future messages. “It’s kind of table stakes for all modern encryption protocols,” Green said.
But not for Twitter. The company further says it has no intent to institute a forward secrecy protocol. “We don’t plan to address this limitation,” it wrote.
To Green, it’s “a big red flag.” Modern encryption is generally based on the open-source Signal Protocol. If Twitter were working like basically every other tech company, it would’ve used this readily available, powerful and well-tested code resource to develop its encryption. This would’ve guaranteed changing encryption keys. The fact that the platform didn’t is “super mysterious.” On it’s own, the lack of forward secrecy is “kind of bad,” said Green, but the broader implication that Twitter went completely in-house and designed it’s own cryptography is even more worrying.
As far as he knows, Twitter doesn’t have many cryptographic experts on staff. After Musk’s purge, the platform doesn’t have that many people on staff, period. Encryption is “a very hard thing to get right,” Green said. If Twitter didn’t build on the existing, open source expertise that’s widely available “maybe they made it up themselves, and that’s where people make big mistakes,” the JHU professor added.
Both Green and the company’s blogpost expressed hopes that Twitter’s encryption feature will improve down the line. But the forward secrecy failing gives the security expert pause. If Twitter has made mistakes independently developing this first release of secure messaging, those issues will reverberate throughout the platform in perpetuity. “It seems like they made some foundational choices that might not be great,” Green said. “If you build a bad basement on a house, you’re gonna be fighting with problems forever.”
